This document is a simple example and/or case study of how to use AHA-GUI to aid in reducing attack surface of a scanned host.
Understanding attack surface is a key in reducing system complexity and exploitability. In combination with standard attack surface reduction techniques, AHA-Project tools can help identify, understand, and reduce attack surface.
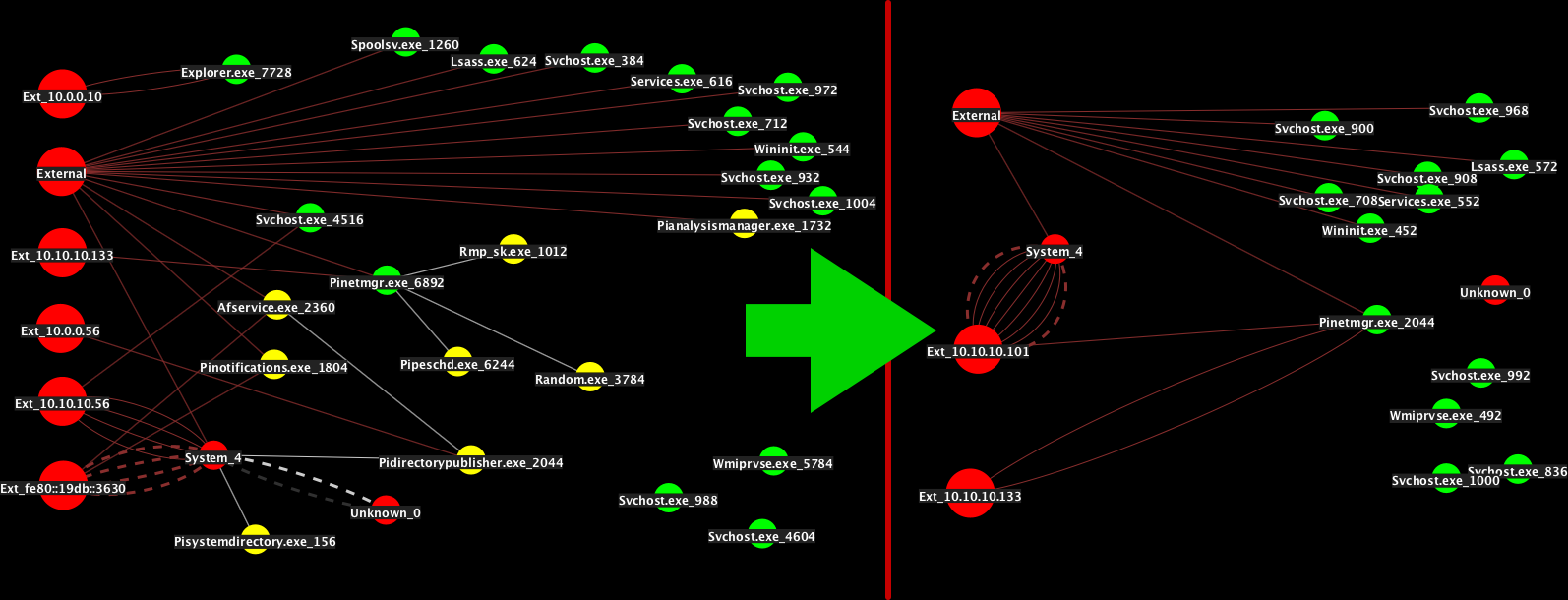
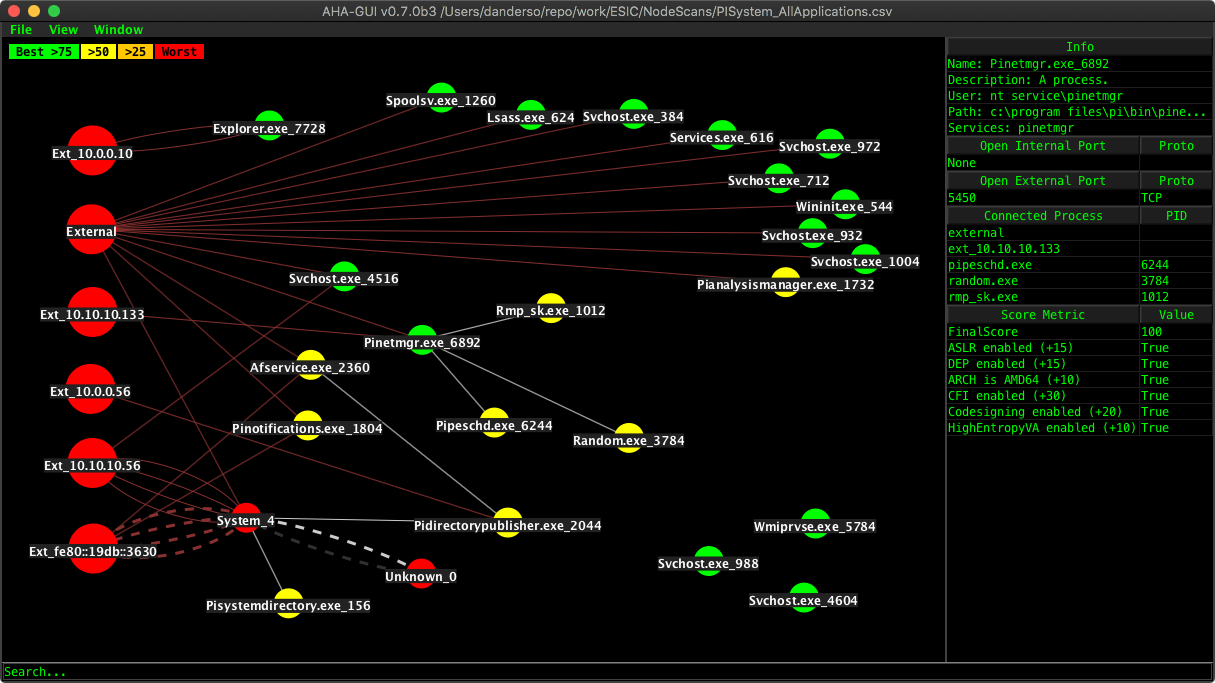
This image above shows a VM prior to any common attack surface reduction practices being employed. We can see there are many processes on the machine, lots of system processes, and several application processes.
Two hardening techniques will be applied here:
- One Application per VM
- The suite of applications being studied allows for them to be easily split between VMs. In this case, some of the companion applications should be moved to other VMs, to reduce attack surface and provide isolation between the different application functions should it be compromised.
- Removal / reduction of superfluous operating system processes
- Uninstall/Removal of svchost based services that are not needed
- Removal of the print spooler
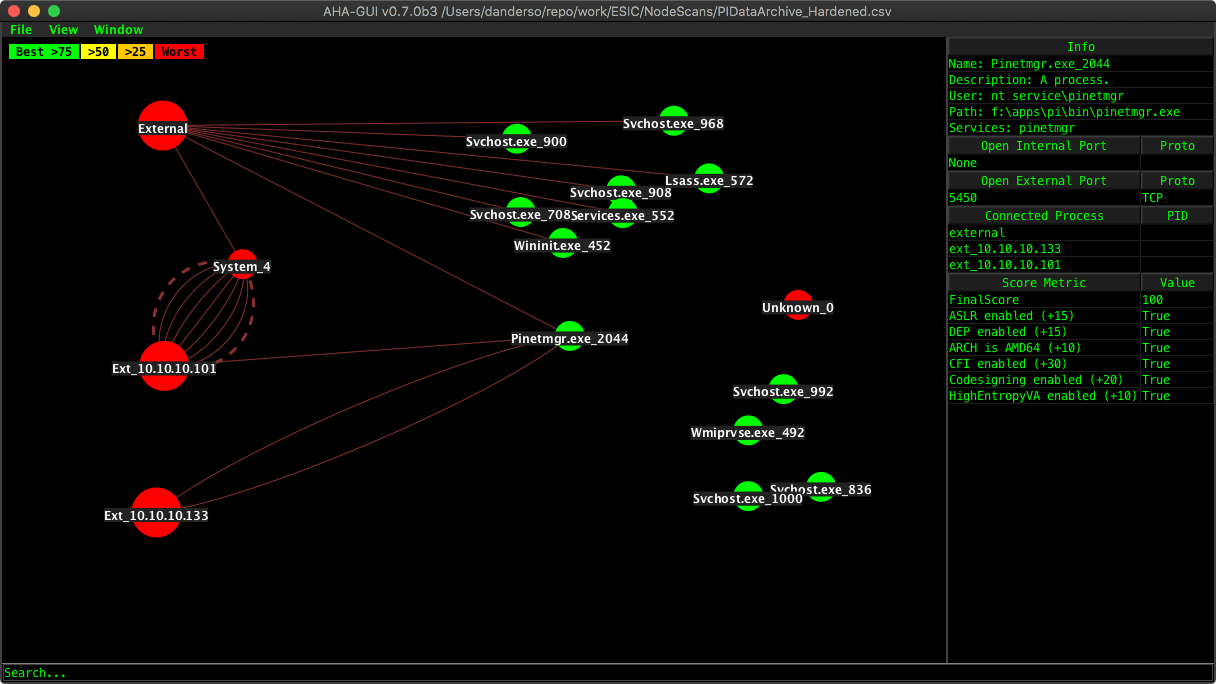
After applying the stated methods, we can re-scan using AHA-Scraper and view in AHA-GUI to see that the number of processes has been dramatically reduced.